Integration Resources
Datasheet
Whitepaper:
Support Documentation:
LOGbinder and Logsign: Better Together
Logsign has developed a custom LOGbinder for SQL Server integration for more comprehensive SQL database auditing.
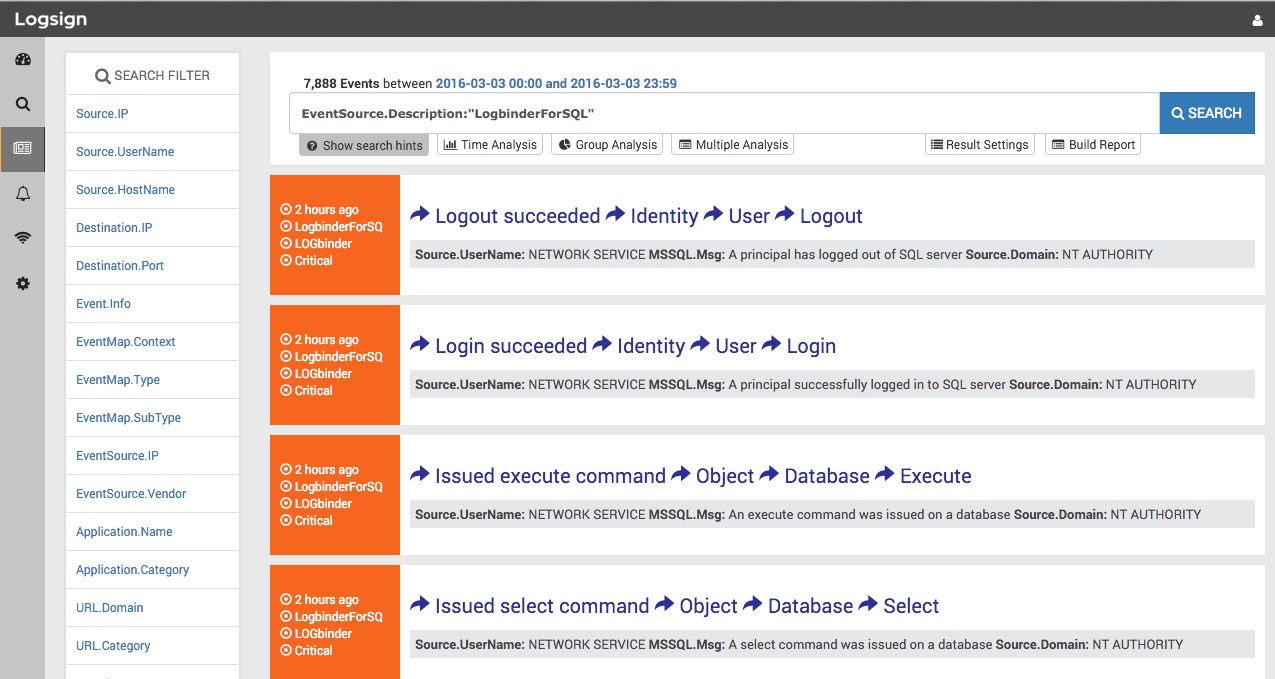
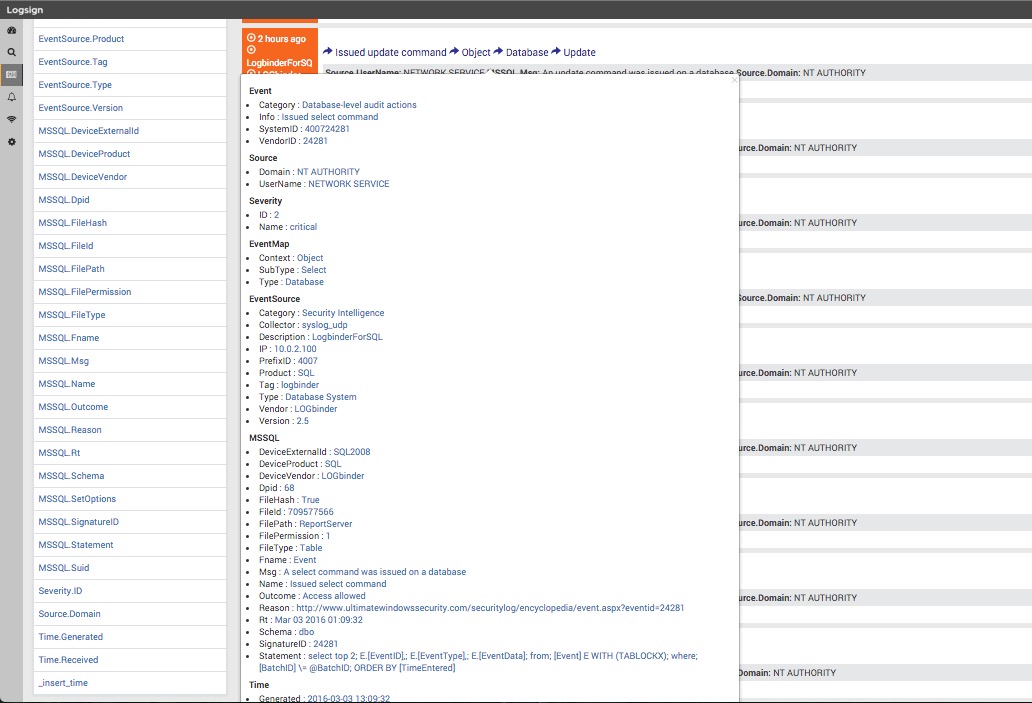
LOGbinder SQL Server collects and normalizes event IDs from Microsoft's SQL Audit feature of SQL Server 2008 and higher. Logsign visualizes LOGbinder's
output via clear dashboards to leverage the centralized alerting, reporting and secure archival of log management.
Create alarms using Logsign advanced alarm module for more than 300+ event IDs instantly!
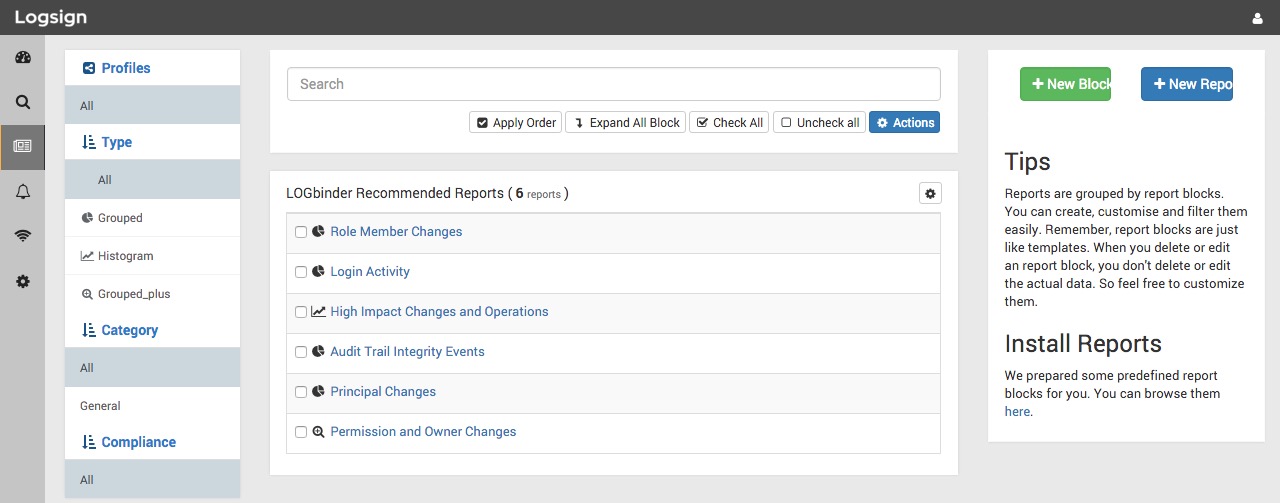
Logsign's custom integration makes security audit reports seamlessly accessible and make practical security monitoring and compliance more feasible.
The integration also saves organizations the trouble of creating their own rules and reports; Logsign automatically generates compliance reports as
soon as logs are collected from LOGbinder.
With Logsign's custom integration you get:
- Quick response via pre-defined Dashboards
- Automated Compliance Reports
- Automated Actions by Alert Modules
- Advanced Search Capabilities.
- Archiving
About Logsign
Logsign is a full feature, all-in-one SIEM solution which unifies Log Management, Security Analytics and Compliance. Built on the NoSQL infrastructure,
Logsign relies on the principle that centralizing log data, analyzing in real-time and providing actionable insights is critical for business continuity.
Logsign delivers a great value and visibility to organisations in the areas of Compliance, Security and Log Management. Logsign core features are Log and
Event Data Centralization, Event Correlation and Historical and Real-Time analysis. At the base of Logsign lies data storage using embedded HDFS and NoSQL
indexing. Collecting data out-of-the-box is Logsign core ability to track, audit and correlate critical security events. Logsign aggregates system, network
and audit logs from various sources. These can be firewalls, routers, IDS/IPS, network devices, Windows, Linux/Unix, databases, VMware ESX, mail servers,
web servers and many more. These devices and logs generate messages that include authentication, network and security activity, system changes and more.
A unified platform with a “single-view” feature allows quick reviews. It provides more than hundreds of predefined correlation rules out-of-the-box to
solve most of the critical log and event monitoring needs fast. Organizations get better at detecting fraud and other attacks by using Logsign algorithms
to mine historical information in real time. Beyond correlation, Logsign automates remediation steps with active built-in responses. Learn
more at www.logsign.com.