Free Active Directory Change Auditing
No matter how big or small you are, whether you have budget or not – you need to be monitoring changes in Active Directory.
The Windows Security Log and Active Directory auditing faithfully log a cryptic and noisy trail of security significant changes
made anywhere in Active Directory. But there's no good way to report or visualize this data.
To address this gap we've combined
- our deep knowledge of the cryptic Windows Security Log
- a free edition of our SuperCharger for Windows Event Collection
- the power of Splunk
to give you easy but powerful visualization of security signicant changes in Active Directory with the power of Splunk Free while
staying under the Splunk's 500mb per day limit.
Get started now
Leverage Native Windows Event Collection with Supercharger
Our Free Active Directory Change Auditing Solution leverages the power of native Windows Event Collection to
- Filter out the noise and collect only those events from each domain controller's security log that represent significant security change.
This is usually less than 0.1% of the log. We do this with a managed security log filter that comes with Supercharger for
Windows Event Colllection which is free for use with manange domain controllers.
- Collect these change events from each domain controller to one central server. No agents to install. No remote collection. No credentials or holes to
open in Windows Firewall - WEC is zero touch. And when you install a domain controller, it automatically begins sending events.
That's the beauty of native Windows Event Collection managed by Supercharger.
Get started now
Leverage Splunk to Refine Cryptic and Noisy Audit Events
Once WEC delivers these events to Splunk, our LOGbinder for Splunk App leverages our
deep experience with the Windows Security Log
to refine the raw and cryptic logs into easy to understand dashboards that help you zero in on the important changes in AD,
who made them and when.
Too often Splunk Apps are lopsided. Apps are either written by someone who knows Splunk but is not an expert in the
particular logs the app pertains to. Or the author is a subject matter expert in the logs being analyzed but isn't
a Splunk expert. This leads to predictable results.
Our Splunk App for LOGbinder is a collaboration between security log SME Randy Franklin Smith and talented Splunk engineers
that uses advance features of Splunk to do more than just filter raw events.
Get started now
Highlights of what makes the app special
To make this app work we had to make some improvements to how Splunk parses Windows Security Events.
The problem with stuff built by non-specialists is that it suffices for filling in a bullet point like
“native parsing of Windows Security Logs” but doesn't come through when you get serious about analysis.
Case-in-point: Splunk treats these 2 very different fields in the below event as one:
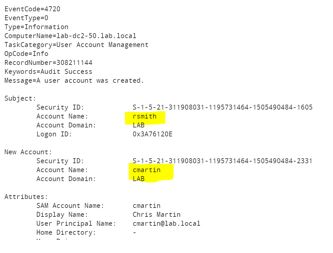
As you can see rsmith created the new user cmartin. But checkout what Splunk does with that event:

Splunk parses the event as though there's no difference between the actor and the target of a critical event like a
new account being created? Here's what the same event looks like once you install our Splunk App:
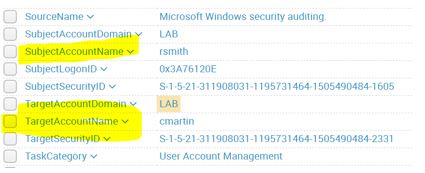
Knowledgeable Splunk engineers may wonder if the app depends on "index time" parsing. And the answer is “no”.
We do it the right way with search time fields extractions. So the app works on old events already indexed
and more importantly doesn't impact indexing. We tried to do this right.
Plus, we made sure this app works whether you consume events directly from the Security log on each
computer or via Windows Event Collection (which is what we recommend with the help of Supercharger).
Start Auditing Active Directory Now
To get started