Collectors
A collector is simply a Windows server running the Windows Event Collector service. WEC also depends on the Windows Remote Management and Windows Event Log services (see
Services). The Windows Event Log service is already configured and automatically started. WinRM and WEC are activated by an initial execution of “winrm quickconfig” and then “wecutil quickconfig” (see Tools).
To begin collecting event logs, a collector needs at least one subscription, which can be created in Event Viewer or with the Wecutil command. Then one or more forwarder computers need to be configured to check in with the collector.
When a forwarder connects via WinRM, it queries the collector for which subscriptions apply to it. The collector compares the forwarder to the allowed source computers defined on each subscription and returns the matching subscriptions. The forwarder begins sending applicable events to the collector which writes them to the destination logs specified in each subscription.
The primary collector-side type of object in WEC is
Subscriptions. ut to support various network scenarios and authentication of non-domain member forwarders, three other WinRM objects come into play:
- Listeners
- Authentication Methods
- Client Certificate Mappings
Every collector has at least one WinRM listener which defines an incoming network channel for communicating with forwarders. If your forwarders are part of the same overall Active Directory environment
(forest and any other trusted domains), you don’t likely need to worry about listeners because the default listener created when your first run “winrm quickconfig” is all you will need.
Listeners are maintained with the
WinRM command (see winrm create winrm/config/listener).
Listeners comprise:
-
Transport – Either HTTP or HTTPS. Default is HTTP, which is encrypted by WinRM in normal circumstances (see
Encryption).
HTTPS requires an appropriate certificate and is normally only required when collecting events from non-domain computers (see
WEC in a Non-AD Environment).
-
Port – The TCP port. Default is 5985 for HTTP and 5986 for HTTPS.
-
Address – Default is * which corresponds to all IP addresses on the collector. Otherwise specify an IP address prefixed by “IP:”.
-
Hostname – Default is blank, which means the computer’s DNS name. If the listener is HTTPS, the hostname must match the subject or subject alternative name in the Listener’s certificate.
-
CertificateThumbprint – Only applicable if listener transport is HTTPS. Specifies a certificate from the local machine’s personal certificate store that must meet specific requirements
(see WEC in a Non-AD Environment).
-
Enabled – True or False. Collectors only accept forwarders on enabled listeners.
Each listener must be a unique combination of Transport and Address (e.g. there can only be one HTTP listener on port 10.4.0.1). You normally only need one listener per collector; more are likely to cause confusion and misconfiguration.
Each listener has some dependencies on other configuration items which, if neglected, can cause WEC to silently fail.
-
Firewall - If Windows Firewall is active, each listener needs to be permitted. “Winrm quickconfig” automatically enables Windows Remote Management (HTTP-In) for port 5985.
-
Urlacl - Each listener also requires a URLACL configured via
Netsh. This is automatically handled for the default listener. But if you follow best practices and configure the WinRM and WEC services to run in isolated processes or create additional listeners, URLACLs need to be configured accordingly.
-
Subscription Manager – In order to connect to the desired listener on a collector, forwarder computers must be targeted at it with a special URL comprising the transport, address, hostname and port of the Listener
(see Target Subscription Manager(s)).
The two main mutual authentication methods supported by WinRM (hence WEC) are
- Kerberos – this is enabled by default
- Certificate – this must be enabled to support non-AD WEC environments – such as with Entra-joined Windows 11 forwarders
Unless you are dealing with non-domain forwarders you can probably ignore this section because in an environment where the collector and forwarders are all part of the same AD environment (forest and any other trusted domains), forwarders authenticate to the collector via Kerberos using the computer account in AD. Then WinRM encrypts subsequent event forwarding traffic using encryption based on an initial key exchange accomplished during the Kerberos authentication.
But untrusting (non-domain) forwarders and collectors can’t authenticate each other via Kerberos and must use certificates and public key infrastructure and encryption is provided via HTTPS.
A collector needs to know which Certificate Authorities to accept client certificates from and a local Windows user account to impersonate.
That local account needs access to the destination logs associated with the client certificate (see Subscription
Certificate Authorities).
These requirements are satisfied by creating client certificate mappings on the collector using the WinRM command (see
winrm/config/service/certmapping). Each mapping specifies:
-
Issuer – Thumbprint of the Certificate Authority for forwarders’ client certificates. This certificate must be present in the collector’s Trusted Root or Intermediate Certification Authorities stores .
-
Subject – The DNS name of the forwarder(s). Use wildcards to specify multiple forwarders. For instance, *.acme.com would match hosts’ FQDNs ending with “.acme.com”. The client certificate must specify a matching DNS name in its Subject or Subject Alternative Name attributes.
-
URI – The URI or URI prefix for which this mapping applies. Normally just “*”
-
UserName – Name of a local Windows user account which the collector will impersonate when attempting to access the destination log. This account needs no special authority but must be enabled.
-
Password – Password of the above account. If the account’s password expires the mapping must be updated.
-
Enabled – True or False. Forwarders presenting certificates signed by this mapping’s CA won’t be able to connect unless enabled.
Each mapping must be a unique combination of Issuer, Subject and URI. In addition to the appropriate certificate mapping, the Collector must have client certificate authentication enabled (see
winrm/config/service/auth).
How Supercharger Helps with Collectors
Installing Supercharger's collector component may be the last time you have to logon to that Collector again.
Sit back and manage all you collectors from the central web-based management interface.
Supercharger manages every aspect of Collector configuration, WEC operations as well as monitoring of throughput and health.
Supercharger detects more than 50 different problem conditions and remediates many of them automatically and notifies if necessary.
And with Collector and Subscription policies, managed filters and queries, you don't have to perform repetitive configuration tasks or worry about consistency.
In fact, Supercharger allows you to replace a failed collector in seconds, perfectly configured to take over its responsibilities.
Supercharger Enterprise builds on top of Free Edition features:
Supercharger Enterprise expands on this foundation, providing comprehensive
enterprise management of your global Windows Event Collection environment.
Evaluate Enterprise for 30-days - Keep Free Edition
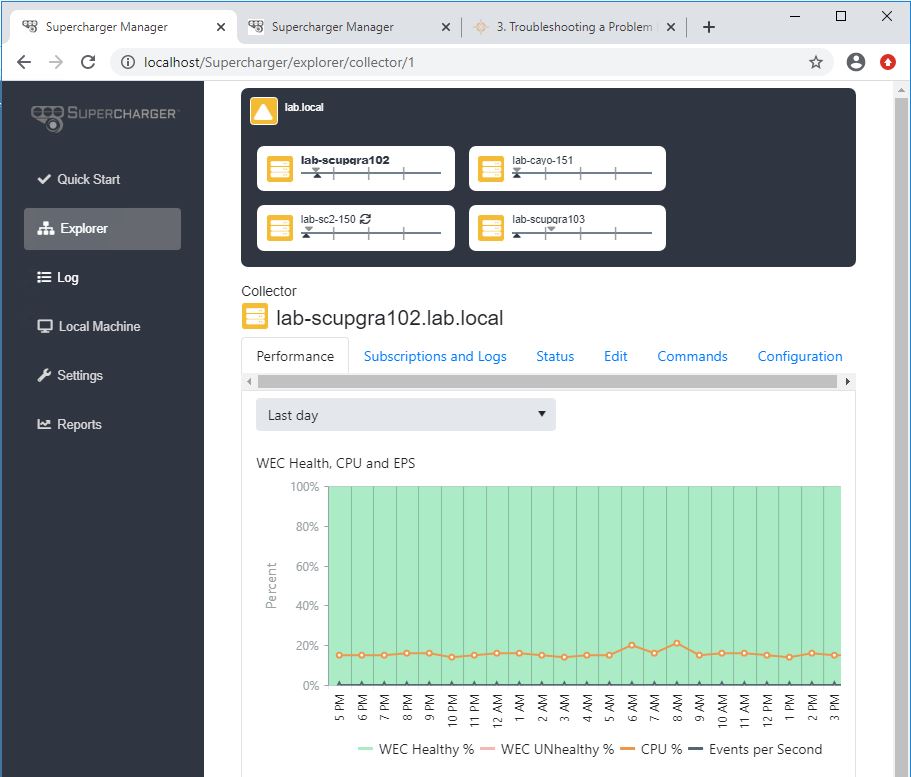
Collector Health
Supercharger monitors every aspect of collector health alerting you via color-coded dashboard,
events sent to your SIEM and optionally email to any issue affecting event log collection. Supercharger detects
if and when WEC becomes overloaded and begins to drop events which could result in lost audit trails or allow
intrusions to go undetected.
Subscription Health
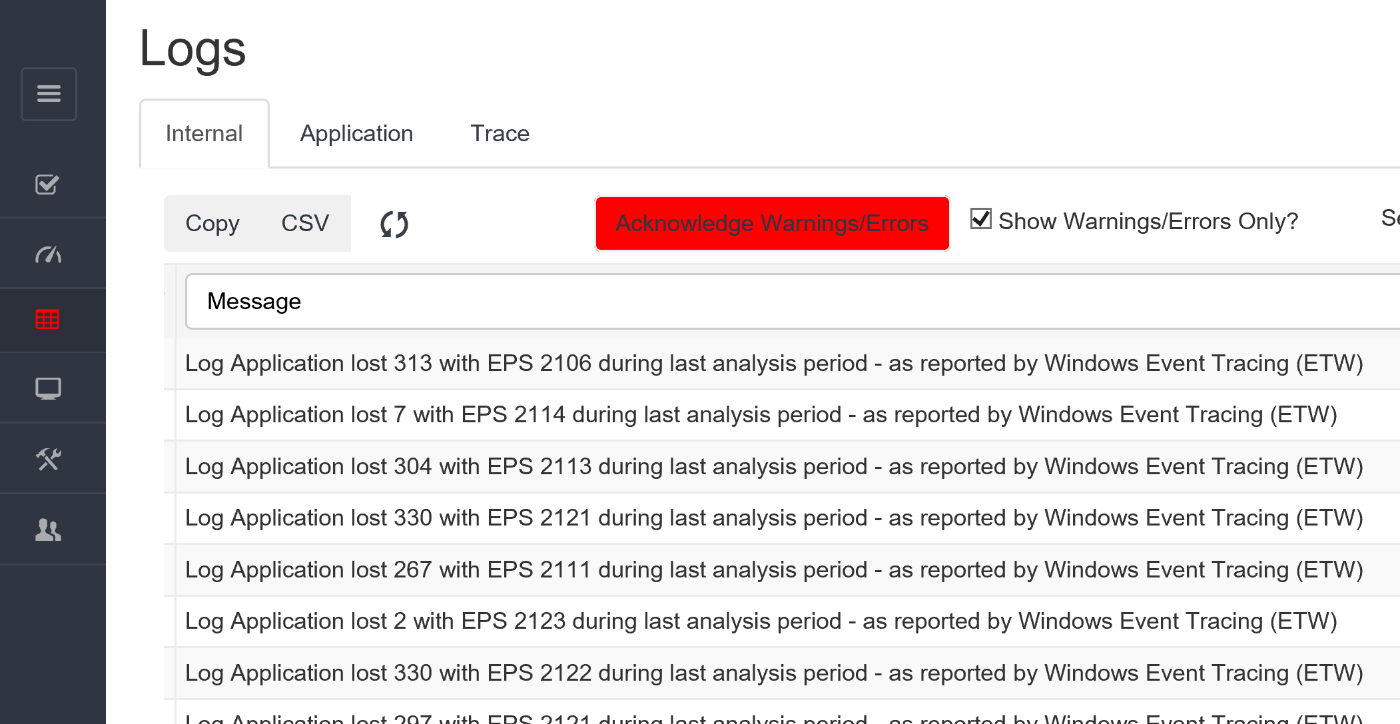
Supercharger monitors the status of every source computer for every subscription
in your environment. Supercharger queries Active Directory for membership of each group assigned to a subscription
and compares these computer accounts to the source computers reported by WEC. After filtering out non-existant,
dormant or disabled accounts Supercharger shows you which endpoints are sending events and which ones are missing. If
percentage of healthy forwarders falls below your specified threshold the subscription goes red and you are alerted.

Boost Throughput and Stability
Out of the box, a Windows Server is not optimized for dedicated Windows Event Collection and above only 2,500 events per second (EPS)
we start to see stability issues and dropped events.
Supercharger can automatically optimize WSMan settings, event logging buffers, the TCP/IP stack and HTTP.SYS settings
to increase EPS by multiple factors while almost eliminating WEC instability issues and dropped events which can
compromise instrusion detection, compliance and audit controls. In our tests we are able to sustain 30,000 events per second.
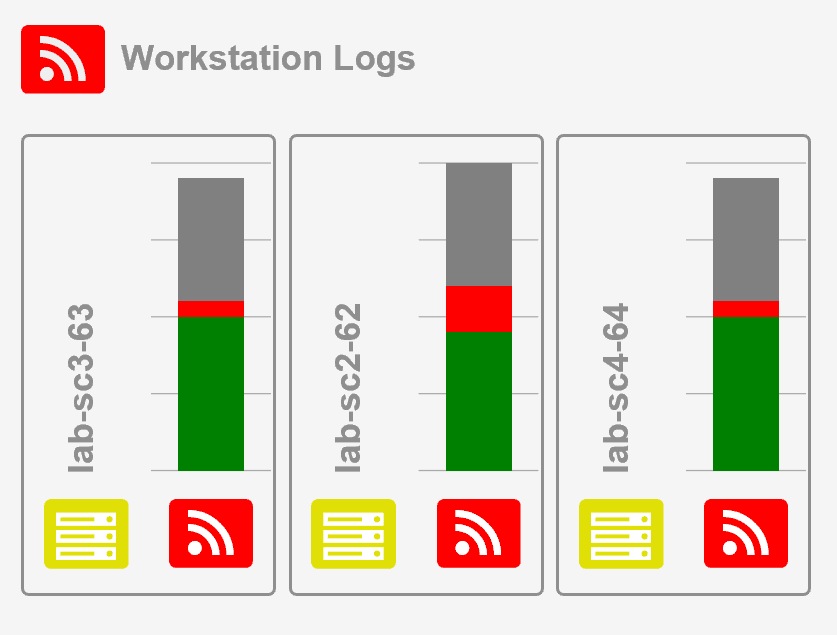
Load Balancing
What if you have tens of thousands of workstations or hundreds of servers that simply produce more events than one Collector can keep up
with?
Supercharger Enterprise can automatically distribute and balance this load across multiple controllers with
Load Balanced Subscriptions.
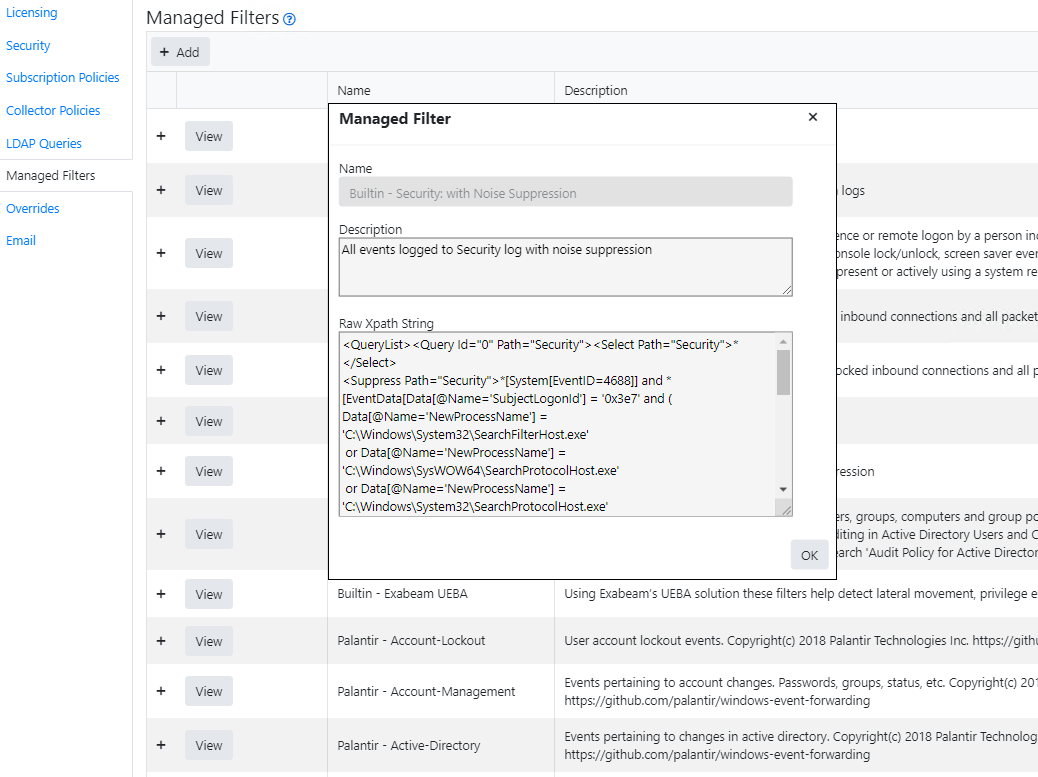
Managed Event Log Filters
One of the most powerful features of Windows Event Collection is its ability to define advanced filters that define exactly
which events you want to forward – and those that are just “noise” and should be left behind.
But building these filters requires specialized knowledge of XML query syntax and of the event logs you are collecting.
Supercharger helps you build powerful filters whether you know XML query and we provide special help for the Security Log
thanks to our relationship with UltimateItSecurity.com. Managed filters are where you find these capabilities.
Once you build your filter you can assign it to multiple subscriptions without duplicating it.
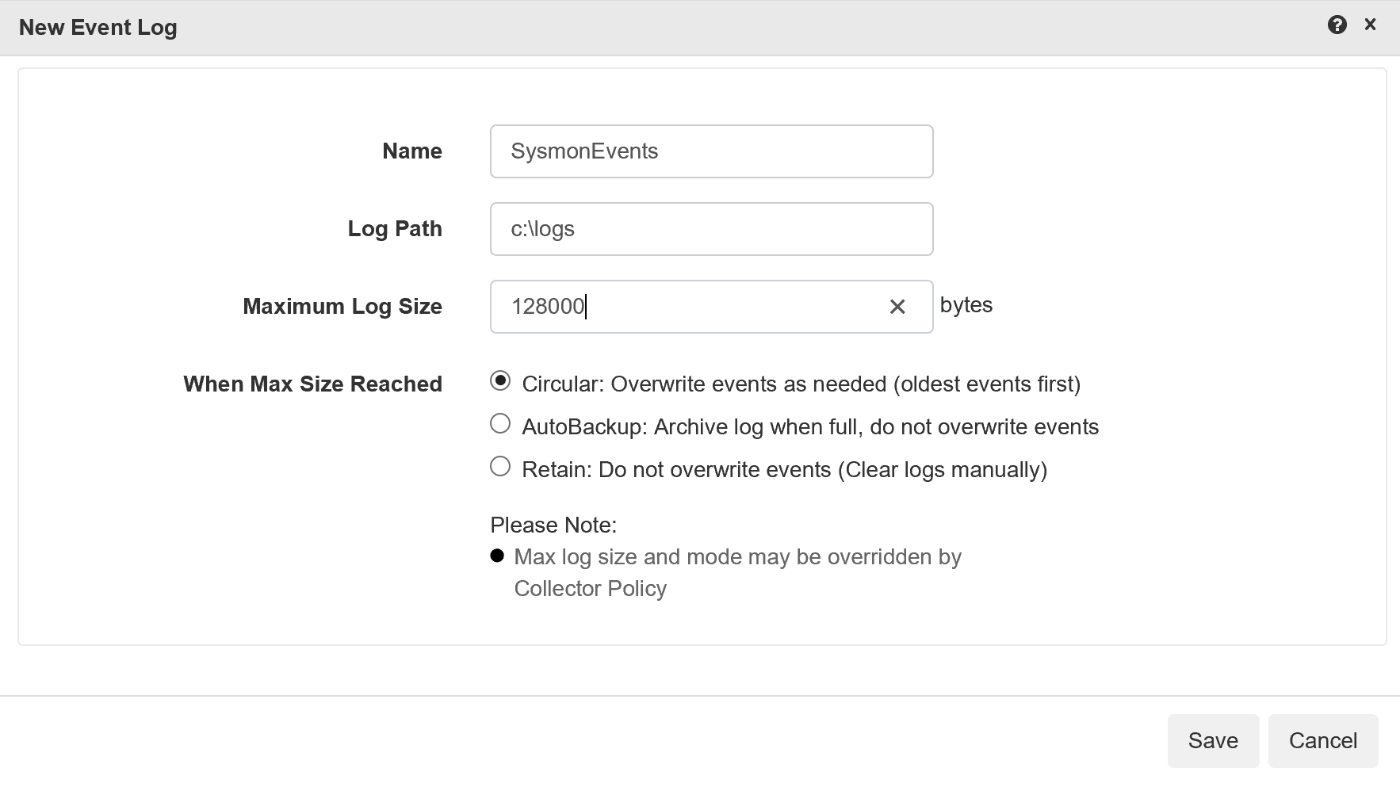
Custom Event Logs
To simplify configuration of downstream configuration and for optimal performance you should maintain a one-to-one
mapping between log types and destination logs on collectors. This requires creation of additional custom event
logs which is a technical and laborious process. Supercharger provides one-click custom log creation.
Purge Old WEC Sources
Event sources records build up indefinitely in the registry which in high-turnover environments become substantial.
WEC never deletes old sources. Supercharger can purge old event sources after a user defined interval.
Policy Based Management
Collector Policies enforce centralized configuration control and can automatically optimize collectors for throughput and dependability.
Subscription Policies ensure subscriptions are configured consistently across your entire environment and allow you to manage
similar subscriptions the same way without duplicating settings.
Security
Role based access control using Active Directory.
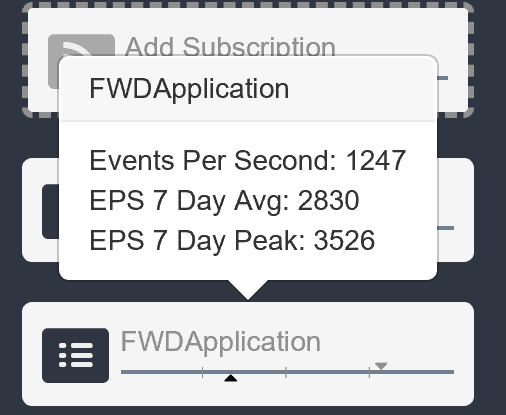
Performance Monitoring
Spot unusual activity levels. Supercharger surfaces key performance counters to the dashboard with visualizations that
plot current activity against 7-day peak and average.
- CPU
- Disk free space
- Events Per Second for each destination log
- Events Lost for each destination log
Capacity Planning
Analyze hourly performance stats to predict when additional collectors will be needed. (coming soon)
Evaluate Enterprise for 30-days - Keep Free Edition
Manage, Scale and Heal Windows Event Collection with Supercharger
Download •
Enterprise Pricing •
Ask Sales