Forwarders
Forwarders (aka source computer) are Windows clients and servers that send event logs to Collectors. Any Windows computer can be a forwarder – no special roles or features need to be installed – and certainly no agents; WEC is built into Windows. A Windows computer becomes a forwarder when you point it at one or more Collectors via the Target Subscription Manager setting. Windows automatically checks in with each collector specified to see if any Subscriptions apply to it and begins forwarding relevant events.
Configuration Requirements
In a typical Active Directory environment, you configure Subscription Manager settings via Group Policy or Intune, and authentication between Forwarder and Collector is automatically handled via Kerberos.
There are a few other configuration tasks that may be necessary on Forwarders depending on your environment.
- WinRM
- Event Log Permissions
- Authentication
Each Collector to which a forwarder may need to send events needs to be configured as a Subscription Manager. (Since it can take time for Group Policy and Intune settings to propagate, you may consider configuring forwarders with all your collectors even if they only find subscriptions on a subset of collectors at this time. If a forwarder doesn’t find any applicable subscriptions on a given collector, there’s no harm.)
In group policy you’ll find this under Computer Configuration \ Administrative Templates \ Windows Components \ Event Forwarding.
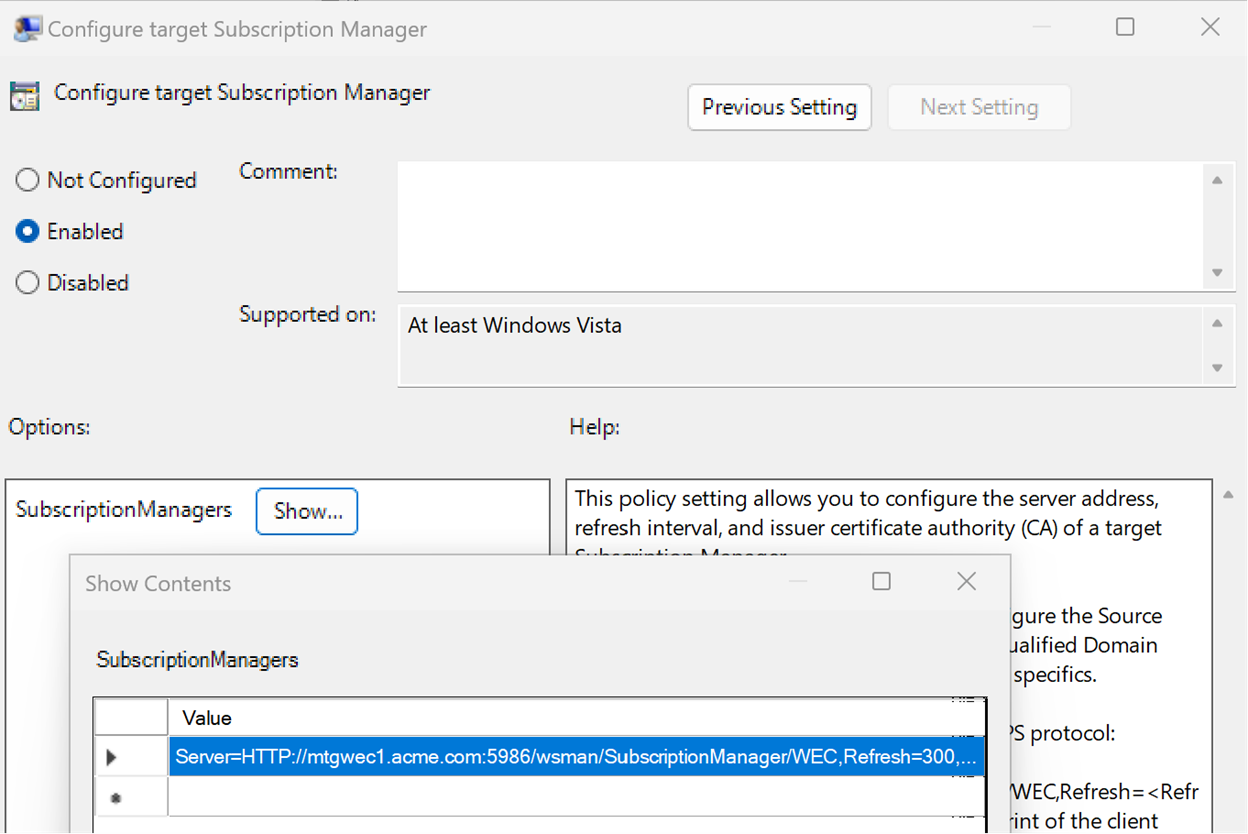
In Intune, you can configure this with a Windows Configuration Profile under Administrative Templates \ Windows Components \ Event Forwarding.
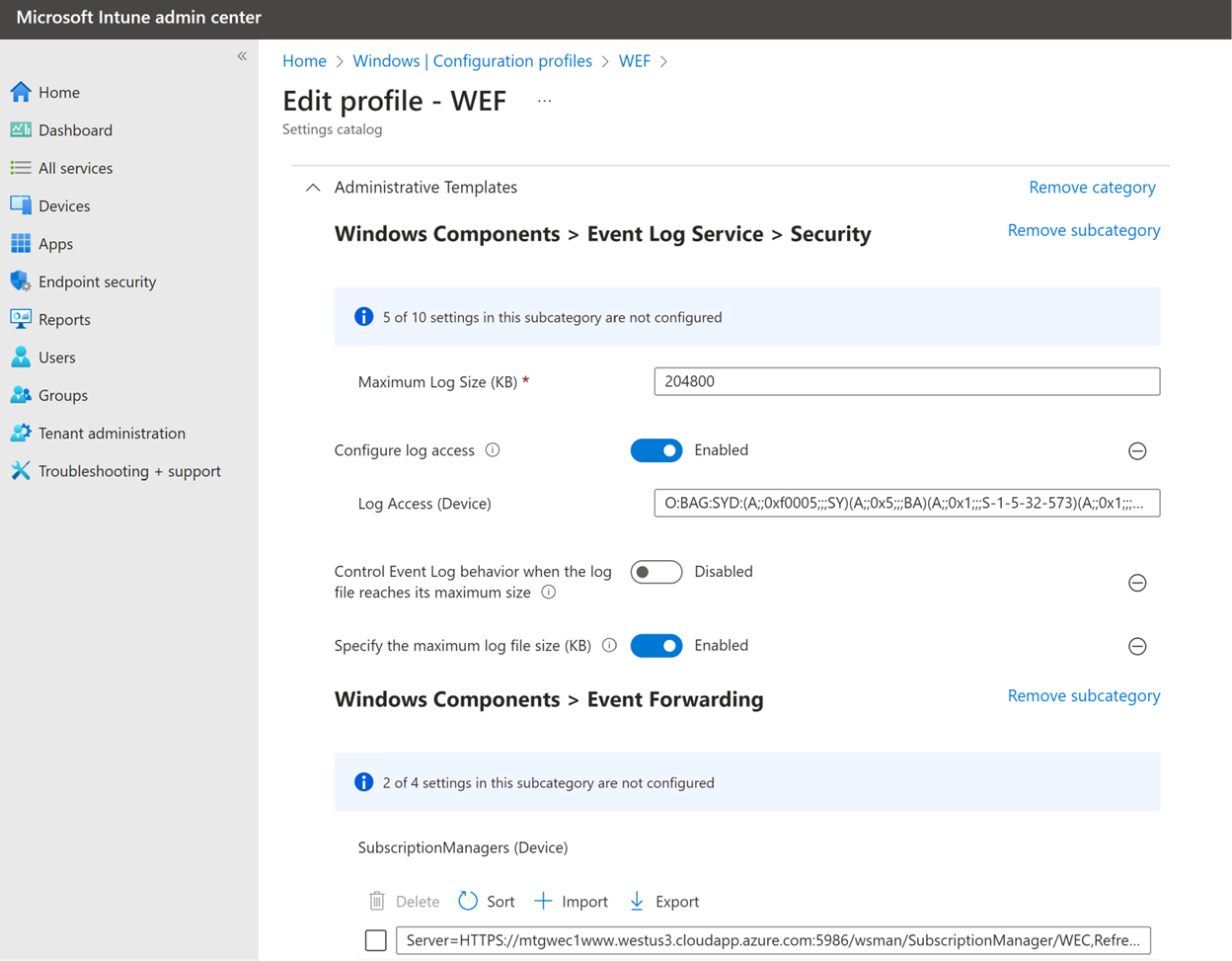
The subscription manager string normally uses the format:
Server=https://<Collector>:5986/wsman/SubscriptionManager/WEC,Refresh=<Seconds>
If you are using client certificates to authenticate forwarders (non AD domain environments) you must also specify the Certification Authority using:
Server=https://<Collector>:5986/wsman/SubscriptionManager/WEC,Refresh=<Seconds>,IssuerCA=<Thumbprint>
The subscription manager string specifies coordinates for the Collector that must match an active listener on that collector, how frequently the forwarder should check for subscription changes and optionally a Certificate Authority for forwarders authenticating with client certificates.
This must correspond to a Listener configured on the collector. Remember that, in an Active Directory domain environment, WEC traffic over HTTP is still encrypted by WinRM. HTTPS requires the collector to have a certificate and private key trusted by all forwarders.
-
FQDN of the collector. The forwarder must be able to resolve this DNS name to the IP address of the collector.
-
TCP Port. Unless you configure a non-standard port on the collector’s listener, specify the default of 5985 for HTTP and 5986 for HTTPS.
-
Refresh interval specified in seconds. This does not affect how often events are forwarded but simply how often the forwarder checks the collector to look for new, changed or deleted subscriptions.
-
IssuerCA (optional). In a normal AD domain environment this will be omitted. See WEC in a Non-AD Environment.
This sample subscription manager string targets the default HTTP listener on wec1.acme.com and causes the forwarder to check in every 5 minutes for subscription changes.
http://wec1.acme.com:5985/wsman/SubscriptionManager/WEC,Refresh=300
If a forwarder isn’t configured with a valid subscription manager string for a given collector, it will never discover applicable subscriptions on that collector.
WinRM
Forwarders need the Windows Remote Management (WS-Management) (WinRM) service to automatically start. Without that, the forwarder will not enumerate the configured subscription manager strings and check in with the corresponding collectors for applicable subscriptions.
You can use Group Policy or Intune to configure WinRM to automatically start. To see a forwarder subscribe to collectors you’ll need to also start the service or wait for the next reboot.
Event Log Permissions
The WinRM service runs as the special principal Network Service which identifies it to network resources, such as a collector, as that computer’s account in Active Directory. This makes it easy to control which forwarders subscribe to which WEC subscriptions simply based on the forwarder’s computer account.
However, the Network Service does not have permissions to read the Windows Security Log by default. (It does automatically have access to Application, System and other Event Logs.) Until you grant Network Service Read access to the Security Log, the forwarder will fail to subscribe to any WEC subscriptions specifying the Security Log as a source.
You can grant these permissions via Group Policy or Intune. In Group Policy look under Computer Configuration \ Administrative Templates \ Windows Components \ Event Log Service \ Security \ Configure log access.
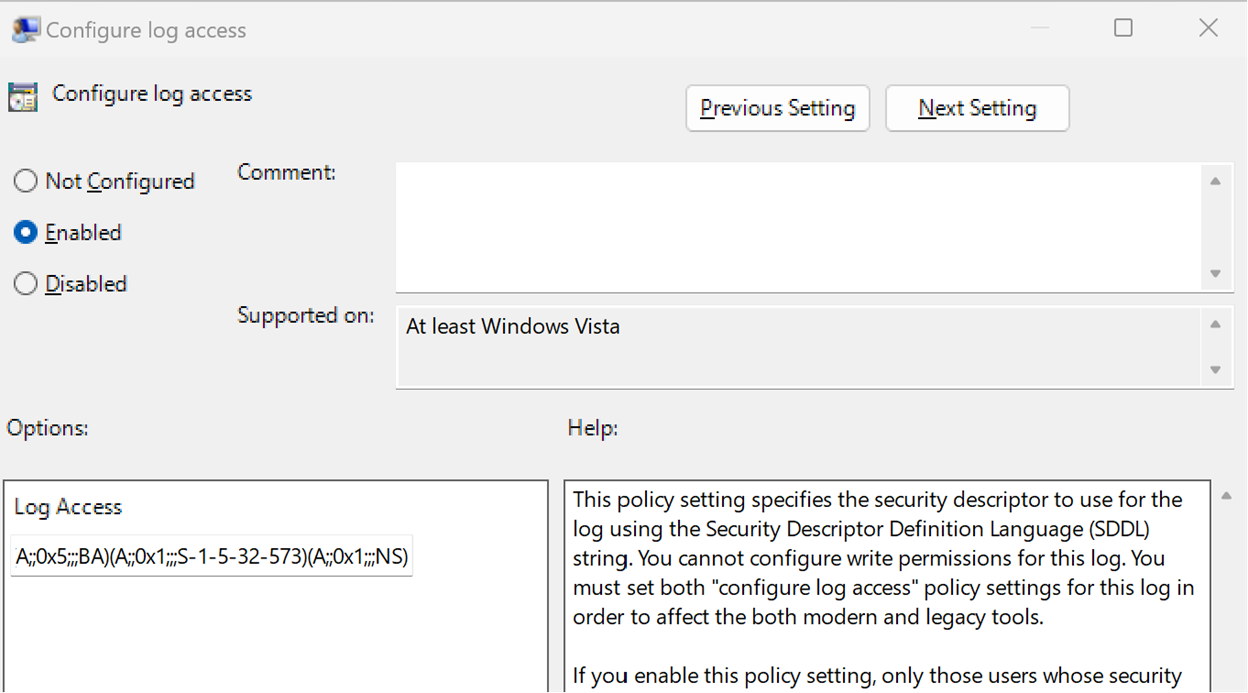
In Intune, you can configure this with a Windows Configuration Profile under Administrative Templates \ Windows Components \ Event Log Service \ Security \ Configure log access.
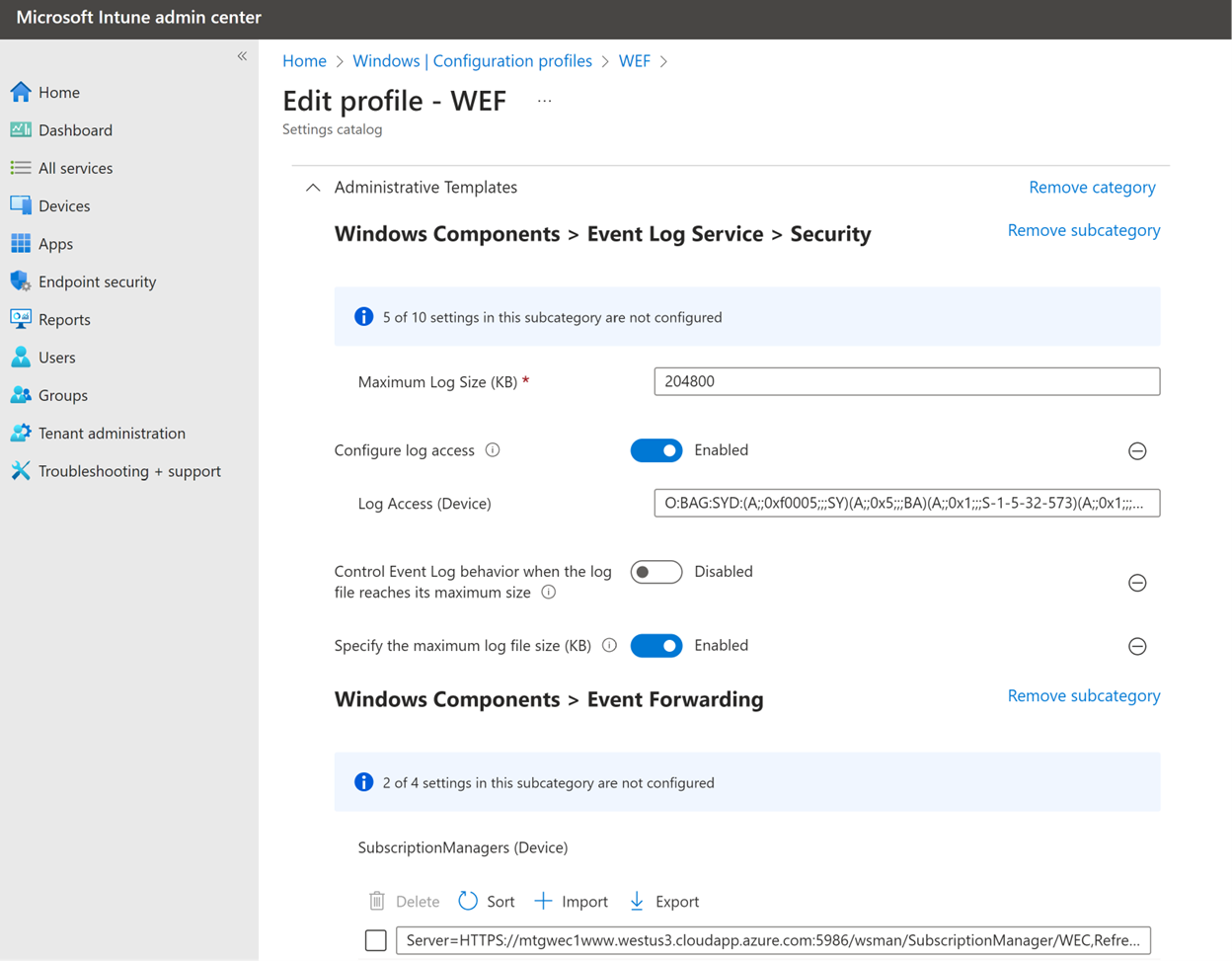
In either case, you specify the permission in SDDL format. The following SDDL string specifies the default permissions on the Security log with an additional entry granting Network Service access:
O:BAG:SYD:(A;;0xf0005;;;SY)(A;;0x5;;;BA)(A;;0x1;;;S-1-5-32-573)(A;;0x1;;;NS)
Authentication
In typical AD domain environments where the forwarder and collector are in domains that trust each other, there is no need to consider authentication because Windows handles it automatically via Kerberos and the computers’ respective accounts in AD.
But if you are forwarding events from a non-AD computer (or if the collector isn’t a member of AD or you are forwarding across untrusted domain boundaries), you will need to use certificates for authentication:
- Server certificate (and private key) on the collector
- Client certificate (and private key) on each forwarder
The certificates have specific requirements in terms of subject names, CA trust, intended purposes, and private key permissions. See
WEC in a Non-AD Environment.
How Supercharger Helps with Forwarders
Supercharger answers the critical questions:
- Which computers should be sending events?
- Which computers are be sending events?
If you can't answer those questions you really have no idea if you are really getting security log data.
To answer those questions, Supercharger compares the forwarder selection criteria on each subscription and then
queries Active Directory and or Entra Id to identify all the matching computers. This answers #1. Then,
to answer question 2, Supercharger compares all the forwarders (aka Event Sources) reported by WEC and their current status
to the results from question 1. Supercharger takes into account the computer's status and "last seen" data in AD or Entra to weed out
dormant computers.
But that's just the beginning of how Supercharger helps you manage forwarders.
Supercharger keeps tract of each forwarder's status and number of events produced by each subscription to which it
belongs to provide a deep audit trail of log continuity and for capacity planning.
Supercharger can even load balance tens of thousands of forwarders between a set of collectors.
Manage, Scale and Heal Windows Event Collection with Supercharger
Download •
Enterprise Pricing •
Ask Sales