Tools and Services of WEC
Here we will explore the utilities and services that comprise Windows Event Collection.
Tools
WinRM command
Windows Remote Management is the underlying component of Windows which handles the network transport, authentication, encryption and authorization of WEC. WEC depends on the WinRM service automatically starting on collector and forwarder. WinRM runs as NETWORK SERVICE and in certificate authentication based WEC scenarios this special principle requires Read permissions to the computer certificate’s private key. On forwarders, WinRM also requires Read permissions to the Security log if you are collecting events from that log.
The WinRM service is configured with eponymous winrm command. Running winrm quickconfig is the easiest way to perform initial configuration of winrm on both forwarders and collectors.
Key WinRM Settings
winrm/config/service/auth
The proper
authentication methods must be enabled in WinRM according to your WEC scenario.
In the case of AD domain environments, Kerberos is already enabled by default. For supporting a non-AD WEC environment – such as with Entra-joined Windows 11 forwarders – client certificate authentication must be enabled. To see the current authentication methods status on a collector, run winrm g winrm/config/service. Here is an example command of enabling certificate authentication: winrm set winrm/config/service/auth @{Certificate=true}.
winrm/config/listener
By default, WinRM opens port 5985 for incoming connections from forwarders to a collector. This is the only listener needed to support AD domain based WEC. To support a non-AD WEC environment – such as with Entra-joined Windows 11 forwarders – you must create an additional
listener. To see the current listeners on a collector, run winrm e winrm/config/listener. Here is an example of creating a default listener: winrm create winrm/config/listener?Address=*+Transport=HTTP.
winrm/config/service/certmapping
For each certificate authority from whom you wish to accept forwarder client certificates, you must link that CA to a non-privileged local user account with a
certificate mapping. To see the current certificate mappings on a collector, run winrm e winrm/config/service/certmapping. Here is an example of creating a mapping: winrm create winrm/config/service/certmapping?Issuer=1212131238d84023982e381f20391a2935301923+Subject=*.example.com+URI=wmicimv2/* @{UserName="USERNAME";Password="PASSWORD"} -remote:localhost.
Wecutil.exe
Wecutil.exe is the command line utility for configuring WEC subscriptions and provides more advanced WEC functionality than what Event Viewer exposes.
Run wecutil quickconfig on a collector to perform initial configuration. Then, there are individual commands for creating, modifying and deleting subscriptions.
List existent subscriptions.
Get subscription configuration.
-
gr (get-subscriptionruntimestatus)
Get subscription runtime status. This command is important for collecting information about each forwarder (aka event source) and its status, such as when it last checked in (heartbeat).
Set subscription configuration.
Create a new subscription.
Delete subscription.
Retry subscription. WEC
subscriptions can occasionally “stall”. We have found that running this command can remediate the situation without restarting the entire collector.
Wecutil can sometimes hang or throw an error. See
WEC operation in Event Viewer, Wecutil or the API throws an error or hangs under troubleshooting.
As
documented earlier, subscriptions have many properties, and you can configure these with Wecutil either via specific command line parameters for each property or via a properly formatted XML file. The
subscription property reference lists each property by its XML tag. Running Wecutil ss /? Provides the command line parameter names:
/e[:VALUE] (enabled)
Enable or disable a subscription. VALUE can be true or false. The default value of this option is true.
/d:DESCRIPTION (Description)
String that describes the subscription.
/ex:DATE_TIME (Expires)
String that specifies the subscription expiration time. DATE_TIME value is specified in standard XML or ISO8601 date-time format: yyyy-MM-ddThh:mm:ss[.sss][Z], where T is the time separator and Z indicates UTC time.
/uri:URI
String that specifies the type of the events consumed by the subscription. The address of the event source machine along with the URI uniquely identifies the source of the events.
/cm:CONFIGURATION_MODE (ConfigurationMode)
String that specifies the configuration mode. CONFIGURATION_MODE can be one of the following strings: Normal, Custom, MinLatency or MinBandwidth. The Normal, MinLatency, and MinBandwidth modes set delivery mode, delivery max items, heartbeat interval, and delivery max latency time. The /dm (DeliveryMode), /dmi (DeliveryMaxItems), /hi (HeartbeatInterval) or /dmlt (DeliveryMaxLatencyTime) option may only be specified if the configuration mode is set to Custom.
/q:QUERY (Query)
String that specifies that query string for the subscription. The format of this string may be different for different URI values and applies to all sources in the subscription.
/dia:DIALECT (Dialect)
String that specifies the dialect the query string uses.
/cf:FORMAT (ContentFormat)
String that specifies the format of the returned events. FORMAT can be Events or RenderedText. When the value is RenderedText, the events are returned with the localized strings (such as event description) attached to the event. The default value of FORMAT is RenderedText.
/l:LOCALE (Locale)
String that specifies the locale for delivery of the localized strings in RenderedText format. LOCALE is a language/country culture identifier, for example, "en-US". This option is valid only if /cf (ContentFormat) option is set to "RenderedText".
/ree[:VALUE] (ReadExistingEvents)
Specifies which events are to be delivered for the subscription. VALUE can true or false. When the VALUE is true, all existing events are read from the subscription event sources. When the VALUE is false, only future (arriving) events are delivered. The default value is true for an /ree option without a value. If no /ree option is specified, the default value is false.
/lf:FILENAME (LogFile)
String that specifies the local event log used to store events received from the event sources.
/pn:PUBLISHER (PublisherName)
String that specifies the publisher name. It must be a publisher which owns or imports log specified by /lf (LogFile) option.
/dm:MODE (DeliveryMode)
String that specifies the delivery mode. MODE can be either pull or push for collector initiated subscriptions and only push for source initiated subscriptions. This option is valid only if /cm (ConfigurationMode) option is set to Custom.
/dmi:NUMBER (DeliveryMaxItems)
A number that specifies the maximum number of items for batched delivery. This option is valid only if /cm (ConfigurationMode) is set to Custom.
/dmlt:MS (DeliveryMaxLatencyTime)
A number that specified the maximum latency in delivering a batch of events. MS is the number of milliseconds. This option is valid only if /cm (ConfigurationMode) is set to Custom.
/hi:MS (HeartbeatInterval)
A number that specifies the heartbeat interval for push subscriptionsm, or the polling interval for pull subscriptions. MS is the number of milliseconds. This option is valid only if /cm (ConfigurationMode) is set to Custom.
/tn:TRANSPORTNAME (TransportName)
String that specifies the name of the transport used to connect to remote event source. It can be http or https.
/esa:EVENT_SOURCE (EventSourceAddress)
Specifies the address of an event source. EVENT_SOURCE is a string that identifies a machine serving as a source of events using fully-qualified domain name, NetBIOS name, or an IP address. This option should be used with /ese (EventSourceEnabled), /aes (AddEventSource), /res (RemoveEventSource), or /un (UserName) and /up (UserPassword) options.
/ese[:VALUE] (EventSourceEnabled)
Enable or disable an event source. VALUE can be true or false. This option is allowed only if /esa (EventSourceAddress) option is specified. The default value of this option is true.
Wevtutil
Wevtutil is Windows’ command for managing event logs and related objects such as publishers. Wevtutil commands include
- el | enum-logs List log names.
- gl | get-log Get log configuration information.
- sl | set-log Modify configuration of a log.
- ep | enum-publishers List event publishers.
- gp | get-publisher Get publisher configuration information.
- im | install-manifest Install event publishers and logs from manifest.
- um | uninstall-manifest Uninstall event publishers and logs from manifest.
- qe | query-events Query events from a log or log file.
- gli | get-log-info Get log status information.
- epl | export-log Export a log.
- al | archive-log Archive an exported log.
- cl | clear-log Clear a log.
Wevtutil is particularly important to WEC management for 2 tasks
Event Viewer
This well-known Windows utility provides a limited GUI interface for managing WEC subscriptions.
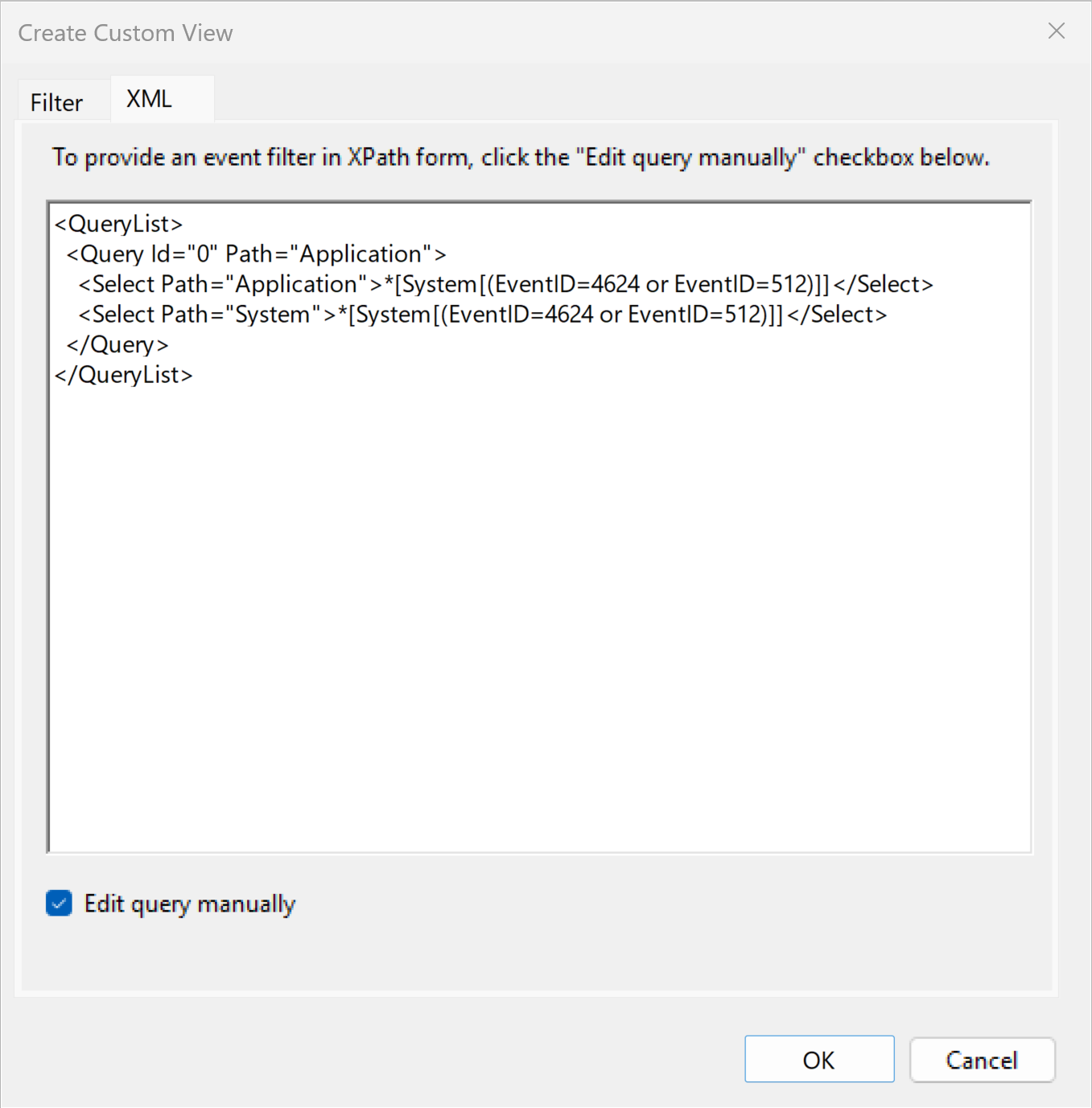
Event Viewer’s key value to WEC management is for testing xpath queries before deploying subscriptions. By testing the xpath query as an Event Viewer XML filter you can
- catch any syntax or formatting errors in your query
- test your logic, verifying the correct events are included or excluded
To obtain the basic formatting for a simple query, first select a log in Event Viewer, then click Filter. Enter any criteria such as Event IDs in the dialog, then click the XML tab. To test a query involving multiple source logs, right click on Custom Views and then Create…
Netsh
This command is relevant to WEC in the particular case where you configure the WEC and WinRM services to run in their own process instead of a shared svchost.exe process. The specific principal SIDs of these services need to be granted access in the ACL of the URL corresponding to each WinRM
listener. https://learn.microsoft.com/en-us/troubleshoot/windows-server/admin-development/events-not-forwarded-by-windows-server-collector.
Services
Windows event forwarding depends on three Windows services. Two of them, Windows Remote Management (WinRM) and Windows Event Log, are necessary on both forwarders (aka event sources) and collectors. As the name suggests, the Windows Event Collector service is only applicable to the collector.
Windows Remote Management
The Windows Remote Management (WinRM) service provides the underlying network transport, authentication and encryption for WEC. The WinRM service must be running on both forwarder and collector.
Use the winrm command line utility to configure WinRM – including the execution of winrm qc for initial configuration.
On collectors, we recommend running WinRM in its own discreet process (sc.exe -type= own) for reliability and scaling purposes. See
netsh for making sure URL ACLs for WEC are configured to support this.
WinRM runs as the NETWORK SERVICE special principle which has limited privileges. On forwarders, it is important to
grant NETWORK SERVICE read access to the Windows Security Log if you will be collecting events from there.
If you are using certificates on forwarders or collectors (see non-AD WEC environments) WinRM (i.e. NETWORK SERVICE) needs Read access to the private key of the computer’s certificate. You can do this on a few systems manually with the Certificates MMC snap-in but larger environments require a custom PowerShell script.
Windows Event Collector
As the name suggests, this is the principal component of Windows that provides Windows Event Collection. The WEC service is heavily dependent on the
WinRM service. This is a collector only service, there is no need for the WEC service on forwarders.
Use the wecutil command line utility to configure subscriptions and to initially set up WEC by running wecutil qc.
On collectors, we recommend running the WEC service in its own discreet process (sc.exe -type= own) for reliability and scaling purposes. See
netsh for making sure URL ACLs for WEC are configured to support this.
Windows Event Log
This is a critical service on both forwarders and collectors, but there is nothing to configure or manage – this is one service that “just works”. The only known issue with WEC and event logs is the occasional problem of
stalled event logs.
Manage, Scale and Heal Windows Event Collection with Supercharger
Download •
Enterprise Pricing •
Ask Sales